Encrypted Data Availability (EDA): Concepts and Cryptography
Here, learners explore how encrypted data availability works and the cryptographic tools behind it. The module covers encryption, erasure coding, polynomial commitments, and sampling methods that enable data to remain confidential yet verifiable. It highlights real implementations like Avail’s Enigma upgrade and compares emerging approaches such as EigenDA and Walacor.
Defining Encrypted Data Availability
Encrypted Data Availability (EDA) introduces a new layer of privacy to modular blockchains by ensuring that data required for verification is publicly available yet unintelligible to unauthorized parties. Unlike traditional data availability solutions, where transaction data is posted in plaintext for all participants to read, EDA encrypts this data before it is published. This approach preserves the security guarantees of data availability, anyone can verify that the data exists and can reconstruct the chain’s state if necessary, while preventing the disclosure of sensitive information contained within those transactions.
The defining characteristic of EDA is its dual commitment: data must remain both available and confidential. Achieving this duality requires two key mechanisms. First, the data is encrypted using keys controlled by a defined group of authorized participants or governed by smart contract logic. Second, cryptographic proofs are used to demonstrate that the encrypted data is fully available on the network without exposing its contents. This combination allows public validators to ensure network integrity while enabling only approved entities to decrypt and process the information.
EDA is particularly suited for private rollups and regulated applications where transaction details must remain hidden from the general public but verifiable to stakeholders, auditors, or counterparties. It enables enterprises and institutions to harness the scalability of modular blockchains without breaching confidentiality requirements or regulatory mandates.
Core Cryptographic Techniques Enabling EDA
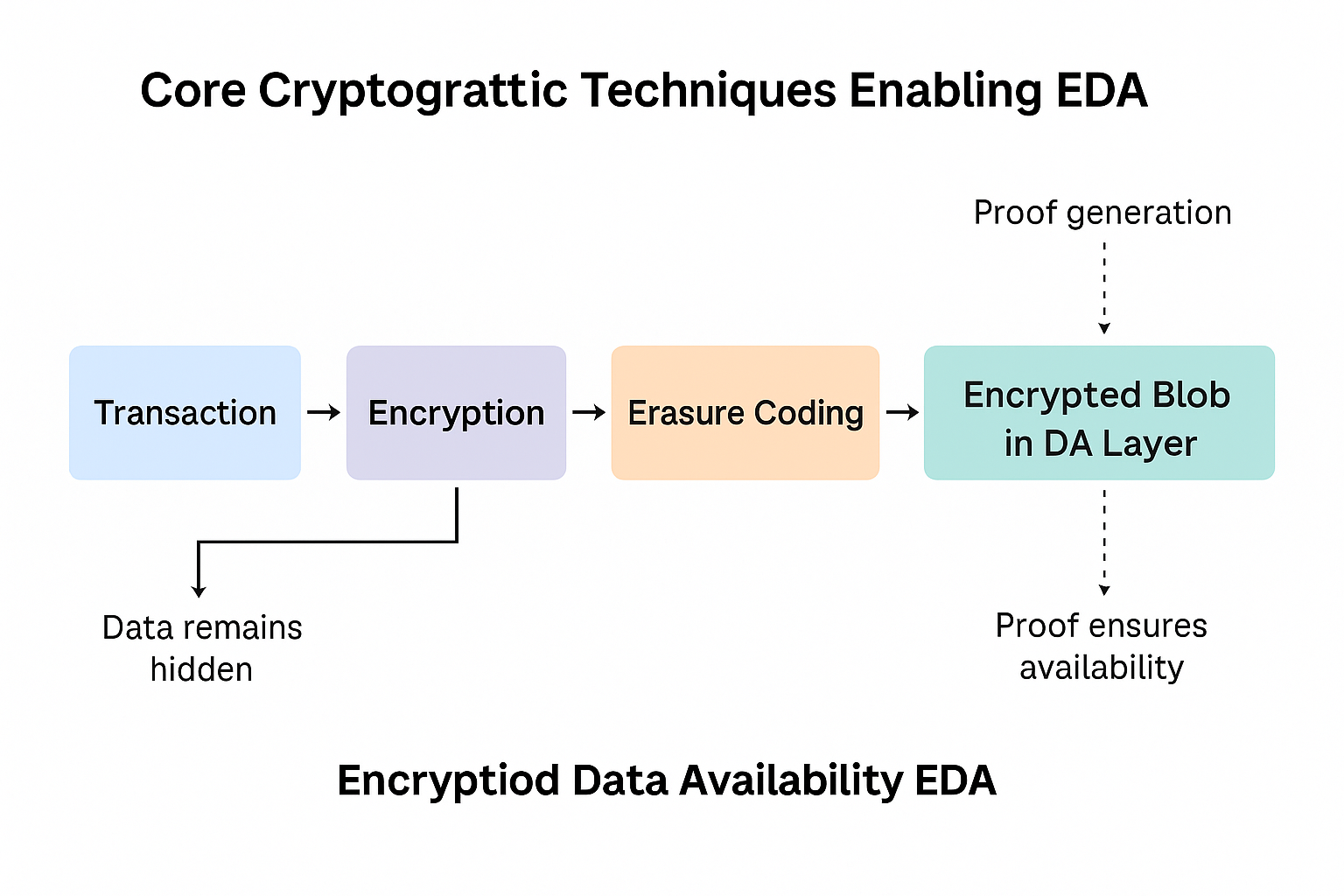
Implementing EDA relies on several advanced cryptographic primitives that work together to balance privacy, integrity, and verifiability. At its core, data encryption is performed before submission to the data availability layer. The encrypted data is often divided into smaller segments and encoded using erasure coding. Erasure coding allows reconstruction of the entire dataset from a subset of its pieces, which means validators do not need to download the full encrypted dataset to confirm its availability. This method is already employed in public DA layers like Celestia and is extended to encrypted blobs in EDA systems.
Another cornerstone of EDA is the use of polynomial commitment schemes such as KZG (Kate–Zaverucha–Goldberg) commitments. These commitments enable light clients to verify that sampled pieces of data are consistent with the entire dataset, even when the data is encrypted. When combined with data availability sampling, validators can probabilistically confirm that all encrypted data is available without having to decrypt it. This design ensures that malicious sequencers cannot withhold data while pretending to have published it.
Key management introduces an additional layer of complexity. In public rollups, no special key handling is required because data is openly visible. In EDA, however, encryption keys must be generated, distributed, and rotated securely. Different approaches exist, ranging from multi-party computation (MPC), where multiple participants collectively manage keys, to threshold encryption schemes that allow decryption only when a defined subset of parties collaborates. Trusted Execution Environments (TEEs) and fully homomorphic encryption (FHE) are also being explored for selective disclosure and computation over encrypted data without exposing it.
These cryptographic techniques together ensure that even though the underlying blobs are hidden from the public, the system retains the ability to prove data availability: a non‑negotiable requirement for rollup security.
The Enigma Upgrade and Emerging Implementations
A major milestone in the evolution of EDA came with Avail’s Enigma upgrade, announced in 2025. Avail, originally designed as a general-purpose data availability layer for modular blockchains, extended its functionality to support encrypted blobs natively. Enigma allows rollups to submit encrypted transaction data while preserving compatibility with Avail’s existing availability sampling protocol. This innovation means that privacy-preserving rollups no longer need to construct bespoke data layers; they can use the same shared DA infrastructure as public rollups while enjoying confidentiality.
The Enigma upgrade also introduced a flexible encryption scheme that supports different governance models. Rollups can choose to manage keys internally, delegate them to consortium members, or use hybrid approaches where certain regulators or auditors have controlled access. This adaptability makes it suitable for enterprise deployments that must balance internal confidentiality with external oversight.
Other projects are pursuing variations of this concept. EigenDA, developed alongside EigenLayer’s restaking ecosystem, is experimenting with privacy features that can be layered onto its restaked data availability service. Walacor has proposed a permissioned DA model that uses encryption combined with consortium-based validation, catering to institutions that prefer tighter access controls over a semi‑public network. Although these implementations differ in architecture and trust assumptions, they share the core principle of encrypting transaction blobs while retaining verifiable availability.
Benefits and Trade‑offs of EDA
The primary benefit of EDA is that it unlocks private rollups without sacrificing the core security properties of rollup architecture. Users gain assurance that transaction data is available for reconstruction while preventing competitors or adversaries from gleaning sensitive insights. This capability is transformative for financial institutions, supply chain networks, and identity systems that need blockchain-grade verifiability but cannot operate in full transparency.
However, EDA also introduces trade-offs. Encryption adds computational overhead and increases latency, especially in environments that require frequent key rotations or threshold decryption. Managing encryption keys securely is non-trivial; compromised keys can lead to catastrophic data leaks. Additionally, selective disclosure, enabling auditors or regulators to view specific data without granting blanket access, is still an evolving area of research and implementation. There are also concerns about interoperability: encrypted blobs are less composable across rollups unless standardized formats and key‑sharing frameworks emerge.
Despite these challenges, EDA represents a crucial step forward in modular blockchain design. As adoption grows, it is likely to become a baseline feature rather than an optional enhancement, particularly as enterprises and governments explore blockchain applications beyond purely public contexts.





