Architecture and Security Models
This section presents the reference architecture for private rollups using encrypted DA and explains how confidentiality, verifiability, and settlement are layered. It examines threat models like key compromise and censorship, explores performance and cost trade‑offs, and discusses how encrypted DA aligns with regulatory requirements such as GDPR and HIPAA.
Reference Architecture for Private Rollups with Encrypted DA
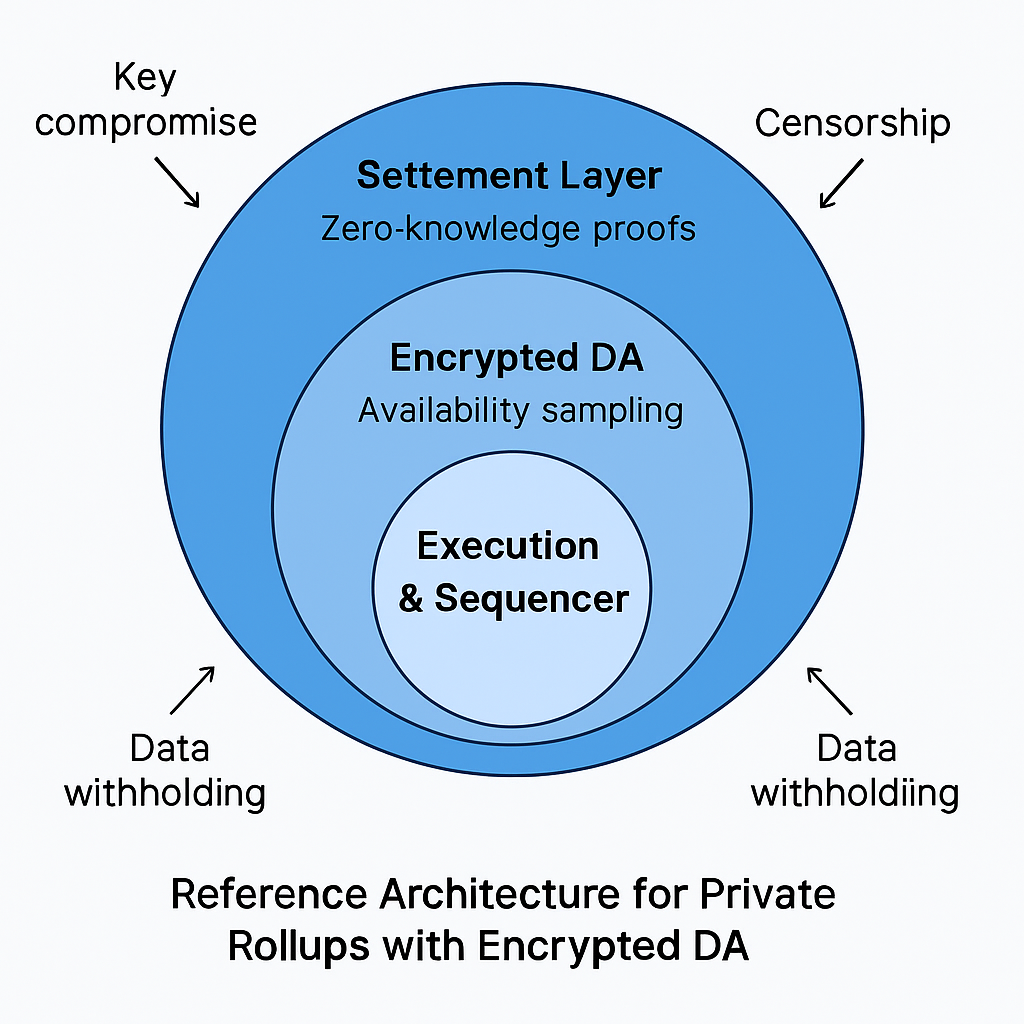
A private rollup leveraging encrypted data availability is composed of multiple layers that work together to maintain both confidentiality and verifiability. At the top lies the execution environment, which may follow either a zero‑knowledge or optimistic design. Transactions are processed here, and state transitions are computed in accordance with the rollup’s smart contract logic. Unlike public rollups, this execution layer does not broadcast transaction details in plaintext; instead, it produces encrypted data packages destined for the data availability layer.
The sequencer serves as the central coordinator, ordering transactions, batching them, and applying encryption before submission. Key management infrastructure operates in parallel to handle encryption and decryption keys. This system can rely on threshold schemes or secure enclaves to ensure that no single actor has unilateral decryption authority. The settlement layer, often Ethereum or a similar base chain, stores commitments to state roots and zero‑knowledge proofs. These proofs enable anyone to verify that state transitions are valid without learning any underlying transaction details.
Finally, the encrypted data availability layer functions as the storage and distribution point for transaction data. Validators in this layer do not need to understand or decrypt the data; their role is to confirm that the encrypted blobs are fully available using data availability sampling techniques. This architecture creates a separation of concerns where confidentiality, integrity, and verifiability are each handled by specialized components, resulting in a modular yet secure system.
Threat Models in Encrypted Data Availability
Introducing encryption into the data availability layer reshapes the security landscape. The most obvious threat is data withholding, where a sequencer or key‑holding party encrypts and posts commitments but refuses to share decryption keys. While availability proofs assure that encrypted blobs exist, withheld keys can prevent legitimate users from reconstructing the state. Mitigating this risk requires carefully designed key governance, including multi‑party control and emergency recovery mechanisms.
Another concern is key compromise. If an adversary gains access to encryption keys, they can decrypt sensitive transaction data, undermining the privacy guarantees of the system. Key rotation and threshold cryptography reduce this risk but add complexity to system design. Metadata leakage is an additional challenge; even if payloads are encrypted, patterns in transaction frequency, blob size, or timing can reveal insights about user behavior. Padding strategies or batching mechanisms are often required to obscure such patterns.
Censorship presents a different category of threat. In modular systems, validators or sequencers might refuse to include certain encrypted blobs, effectively halting specific users or applications. Addressing censorship requires fallback mechanisms, such as alternate sequencers or escape hatches to the base layer, ensuring that users can always exit with their funds even in adversarial conditions.
Performance and Cost Considerations
Encryption adds a computational step to the rollup pipeline, introducing latency and potential throughput limitations. Symmetric encryption algorithms are efficient, but when combined with polynomial commitments and threshold key management, the overall process becomes more resource‑intensive. The cost of data availability also increases because encrypted blobs cannot benefit from certain compression techniques that rely on plaintext patterns.
Despite these overheads, private rollups can still achieve significant scalability gains compared to traditional monolithic blockchains. By separating execution from settlement and availability, they offload much of the burden from the base chain. Furthermore, specialized DA layers like Avail or EigenDA are optimized for high throughput, mitigating some of the additional costs introduced by encryption.
The trade‑off between privacy and cost must be evaluated on a case‑by‑case basis. For applications handling sensitive financial or healthcare data, the added cost of encryption is often justified by regulatory requirements and reputational risk mitigation. For less sensitive use cases, hybrid models, where only certain transaction fields are encrypted, may provide a middle ground.
Compliance and Regulatory Alignment
Encrypted data availability aligns closely with the needs of regulated industries, where privacy is not merely a feature but a legal obligation. Frameworks like the General Data Protection Regulation (GDPR) in the European Union or the Health Insurance Portability and Accountability Act (HIPAA) in the United States impose strict requirements on how personal and sensitive data is stored, transmitted, and audited. Traditional public rollups fail these tests because all transaction data is visible on‑chain, even if pseudonymized.
With EDA, organizations can meet these obligations by ensuring that only authorized entities hold decryption keys. Selective disclosure mechanisms allow regulators or auditors to review relevant data without granting them access to unrelated transactions. This model also simplifies compliance reporting, as on‑chain commitments provide immutable evidence of data integrity while the encrypted payload protects confidentiality.
However, compliance introduces its own challenges. Jurisdictions may require auditable access to encrypted data under specific conditions, creating pressure to design robust key‑escrow or emergency access mechanisms. Balancing these requirements with user privacy and decentralization remains a central design consideration for any private rollup targeting enterprise or government adoption.





