Building the Private Rollup Stack
This module examines the components required to construct a private rollup, including the execution environment, sequencer, key management, and integration with data availability layers. It maps out the flow of encrypted data from users to settlement and explores governance models, access controls, and interoperability challenges when connecting private and public rollups.
Core Components of a Private Rollup
A private rollup stack is structured similarly to a public rollup but incorporates additional layers for encryption, access control, and compliance. At its foundation lies the execution environment, which can be either optimistic or zero‑knowledge in nature. Optimistic rollups rely on fraud proofs to resolve disputes, while zero‑knowledge rollups provide succinct validity proofs for every state transition. Both approaches can integrate encrypted data availability but must handle key management differently during proof generation and verification.
The sequencer is the next critical component. In a standard rollup, the sequencer orders transactions and batches them for submission to the data availability layer. In a private rollup, this sequencer must also perform encryption of transaction data before submission, ensuring that plaintext never leaves the controlled environment. This encryption step can occur locally or within a trusted execution environment, depending on the security model adopted by the rollup.
Key management infrastructure sits alongside the sequencer to handle the generation, distribution, and rotation of encryption keys. Depending on the governance model, these keys may be controlled by a single entity, a consortium of validators, or even distributed using multi-party computation. This design choice determines who can decrypt the data and what trust assumptions the system requires.
The final core component is the interface with the data availability layer. The rollup must submit encrypted transaction blobs to a service like Avail Enigma, EigenDA, or a permissioned DA network such as Walacor. The DA layer stores these encrypted blobs and provides proofs that they are fully available. Validators can use these proofs to confirm that all necessary data is posted, even though they cannot read its contents. This combination of encryption and proof ensures that the rollup maintains both confidentiality and verifiability.
Data Flow in a Private Rollup with Encrypted DA
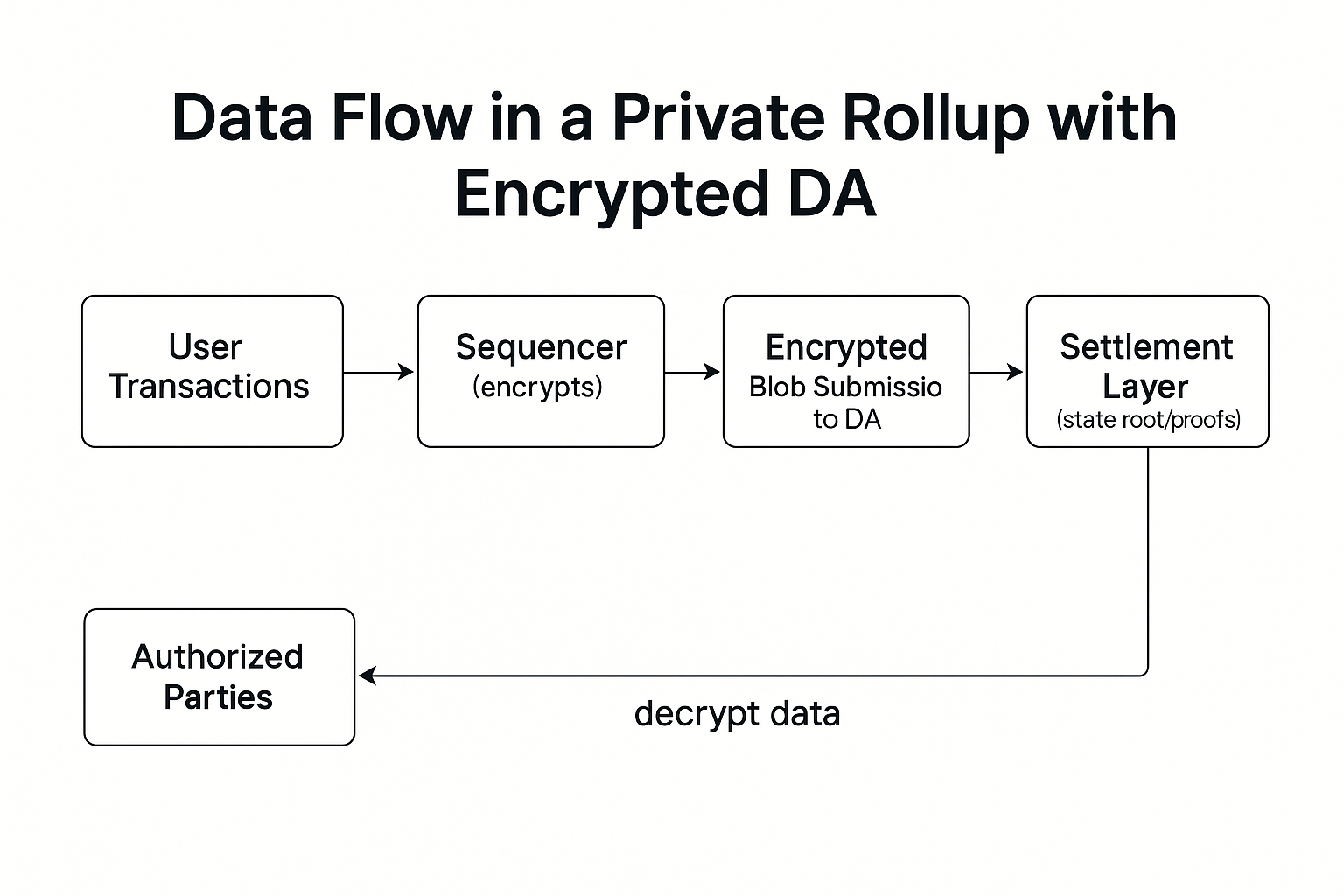
The flow of data in a private rollup diverges from that of public rollups at the point where transactions are batched. In a public rollup, the sequencer aggregates transactions, compresses them, and posts the resulting blob directly to the data availability layer. Anyone monitoring the DA layer can view this blob in plaintext and reconstruct the rollup’s state independently.
In a private rollup, an additional encryption step is introduced. After transactions are batched and compressed, the sequencer encrypts the data using a symmetric or hybrid encryption scheme. The encrypted blob is then submitted to the DA layer, accompanied by cryptographic commitments or proofs that allow validators to confirm its availability without decrypting it. State roots or zero‑knowledge proofs, which do not reveal sensitive details, are posted to the settlement layer (often Ethereum or another base chain) to maintain security guarantees.
When authorized parties, such as consortium members or auditors, need to reconstruct the rollup’s state, they retrieve the encrypted data from the DA layer and decrypt it using the appropriate keys. This process ensures that the network as a whole can confirm availability and integrity while restricting plaintext access to designated participants.
Governance and Access Control
Governance in private rollups extends beyond standard protocol upgrades and parameter changes to include control over data encryption policies. One of the most important questions is: who holds the keys? Some deployments may choose centralized key management, where a single organization or regulated entity controls decryption. While this model simplifies coordination, it introduces a single point of failure and potential regulatory risks if that entity is compromised.
More advanced models distribute key control across multiple parties using threshold cryptography. In this setup, no single participant can decrypt data on their own; a quorum of authorized parties must cooperate to unlock access. This approach enhances security and aligns with consortium‑based governance, where multiple stakeholders collectively manage the rollup. It also supports selective disclosure, enabling different subsets of participants to access only the data relevant to them.
Access control policies must also address scenarios where regulators require oversight. For example, financial authorities may need to audit transaction history without exposing sensitive commercial details to competitors. Private rollups can support such requirements by enabling audit keys that grant read‑only access to specific datasets without compromising overall confidentiality.
Composability and Interoperability
One of the challenges facing private rollups is maintaining composability with the broader modular ecosystem. Public rollups thrive on interoperability; assets and messages flow freely between them via bridges and shared DA layers. Private rollups, by contrast, must carefully manage what information they reveal during cross‑rollup interactions.
Interoperability between private and public rollups is possible but requires encrypted bridging mechanisms. When transferring an asset from a private rollup to a public one, the system must prove that the asset exists and is valid without exposing confidential transaction details. Zero‑knowledge proofs play a central role in enabling this form of selective disclosure. Similarly, private rollups can communicate with each other by exchanging proofs rather than plaintext data, allowing them to collaborate without mutual trust.
Efforts are underway to standardize encrypted blob formats and proof systems to facilitate such interoperability. As these standards mature, private rollups are likely to become first‑class citizens in the modular blockchain landscape, able to interact with public networks while preserving the confidentiality that enterprises demand.





